There is a race going on, and the prize is your wallet. The two contestants constantly vying for the lead are Ransomware and Data Theft.
Ransomware usually depends on untrained employees falling for an email phishing scheme – a phony email that entices the user to click on a malicious link or attachment to release the Ransomware, lock up the system and encrypt the company’s data until a ransom in cryptocurrency is paid. Mostly, these attacks are aimed at Small and Mid-sized businesses (SMBs) for a four or five figure payoff. Big, splashy ones, like last year’s attack on the Colonial Pipeline command millions and make the news.
Data Theft, or Data Breaches require a bit more finesse than Ransomware. Rather than primarily using phishing scams, they rely on phishing, cloud misconfigurations, and credential theft – obtaining end users’ passwords.
So far in 2022 and throughout 2021, credential theft is at an all-time high. According to the annual IBM report ‘Cost of a Data Breach’, credential theft accounts for more breaches than any other tactic.
With so many applications and processes residing in the cloud these days, a user’s password/login credentials provide the quickest route to data breaches. Once a criminal has those credentials, they can barrage your company’s clients, vendors, and partners with phishing emails that appear to come from your business. If you value your reputation, steps must be taken to prevent this.
Once inside your system with stolen credentials, the hacker can cost you money in a lot of ways – they can simply launch Ransomware inside your network, encrypt everything and demand payment to decrypt it. Or they can simply copy or steal all your data and sell it on the Dark Web.
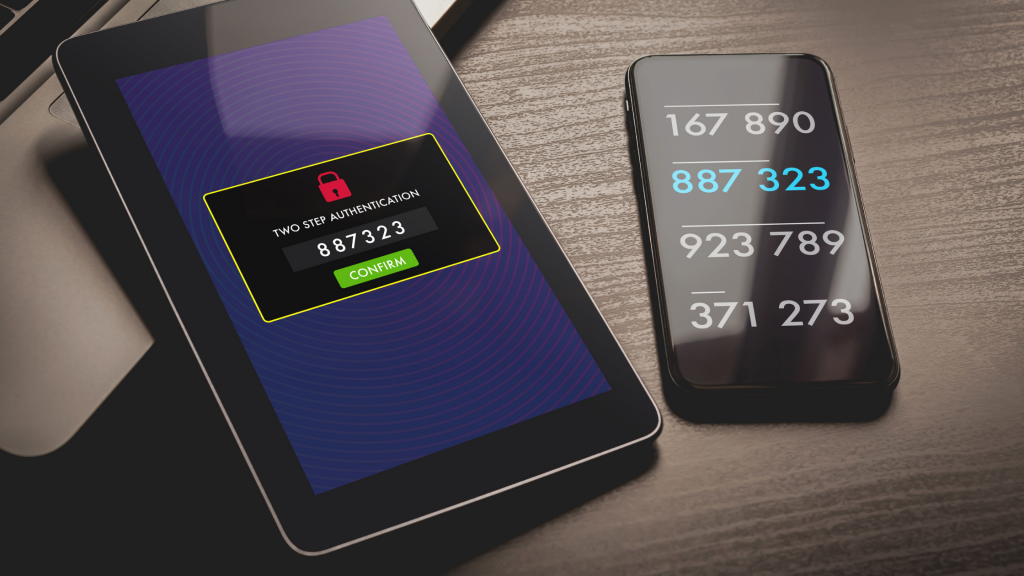
Adding the extra steps of Multi-Factor Authentication makes it much harder to steal employees’ credentials. But which forms of MFA are the most secure? Which are the most convenient?
There are only three main types of MFA, so choosing which to use is not complex.
What are the 3 types of authentication?
Regardless of the MFA method you use, the authentications fall into these three categories:
1) Something you know: Your password/PIN and answers to personal questions (the classic being ‘What is your mother’s maiden name?’). Be careful not to use something you posted on facebook.
2) Something you have. Tokens, scan cards, and smart phones to which an authentication code can be texted.
3) Something you are: Thumb or fingerprint, retinal scan, etc.
These three refer to the type of input required from the end user for authentication. What determines the best Cybersecurity is how this input is entered:
The three main methods of MFA:
1) SMS: code sent to mobile phone.
2) On-device prompt: through an authentication app.
3) Security key: Physically plugged into a device – also available as an app.
Google performed a year-long study comparing these methods to determine which were most and least effective at blocking three types of cyber-attacks:
1) Automated bots
2) Bulk phishing attacks
3) Targeted attacks
The security key blocked 100% of all three types of attacks.
The on-device prompt blocked 91% of targeted attacks, 96% of bulk phishing and 100% of bots.
The SMS-based blocked 76% of targeted attacks, 99% of bulk phishing and 100% of bots.
SMS, the most vulnerable of the three, is the most widely used. For authentication, they text a code to your phone. Once entered in the login screen, you are allowed entry.
The security key, which is the most secure, requires you to plug in a USB device that’s smaller and thinner than a thumb drive. Android and iPhones have a built-in security key. If you are running current versions of Chrome OS, iOS, macOS or Windows, you can use this feature without sticking anything new on your key chain.
Both of these require an extra step, but for the best security, the ‘bother’ of having (and not losing) a small item which easily fits on a key chain should not be viewed as too inconvenient. A successful cyber-attack can cripple a company – even to the point of putting it out of business.
Don’t be lazy! Take the extra step.
Frequently Asked Questions
Q: How do MFA keys work?
A: Hardware keys work essentially the same as other MFA methods: once you login with your credentials, you will then be directed to input the additional factor. Input the code sent or insert your USB key and you gain entry.
Q: What is the difference between 2FA and MFA?
A: MFA uses multiple levels of authentication, starting with the password. 2FA only requires one extra step after the password - usually an identifying question. MFA provides much better login protection.
Q: Is Captcha considered MFA?
A: NO. Captcha forces you to interact with the login simply to prove you are not a bot.
Q: How do I find my MFA settings?
A: For Microsoft Azure users, you can access service settings from the Azure portal by going to ‘Azure Active Directory > Security > Multifactor authentication > Getting started > Configure > Additional cloud-based MFA settings.’ A window or tab opens with additional service settings options.
How secure is your network?
As a reputable member of the IT Support Los Angeles community since 2002, IT Support LA offers a FREE, no-risk network and security assessment. It is a non-intrusive scan that allows us to deliver a comprehensive report that is yours to keep. No strings, and no obligation to ever use our Managed IT Services.
The best defense is the best Cybersecurity to protect your data from theft, and a top-notch Managed IT Services firm to ensure continued reliability and defenses against newly emerging threats.
With our 100% Money Back Guarantee in writing, we offer a risk-free way for prospective clients to try us out. Because we do not require a ‘hard’ contract, our clients can fire us at any time with 30 days’ notice. We have to be good.
Among the Managed IT services we provide:
IT HelpDesk Service
Onsite IT Support
Cybersecurity
Cloud migration and management
Email migration services
Backup and disaster recovery
VoIP phone systems
IT disposition and recycling
Office moves
White label services (IT to IT)
For more information, or to receive your FREE no-risk network and security assessment, just fill out the form on this page or call us at:
818-805-0909

