
Video conferencing has been popular even before the COVID19 pandemic. As the majority of us are forced to work from home, it has now taken the spotlight as nearly the only form of communication involving multiusers.
While this may not be the first pandemic to occur, this is THE FIRST pandemic that has mainly spread through media and social media, to the point that it received the nickname “Infodemic” , which infamously means the false spread of information throughout the internet, causing fear and distance among people.
Unfortunately, the social distancing, along with the sense of fear and confusion among millions of people, presented hackers with a golden opportunity in their continuous cybercrime efforts.
If it seemed that as more and more people are getting familiarized with the various forms of attacks,
COVID19 has presented a new threat to us all and a new way for hackers to keep monetizing on the backs of the users.
The desire to stay informed has led many hackers to release false sites to attract innocents to go to the wrong websites. Specifically, the desire to stay connected has attracted hackers to go after the video conference platforms and one stood up above them all. Zoom.
With 500% surge in daily usage, Zoom has made the popular platform THE BEST and THE FIRST platform to go after.
The main features that made Zoom so popular – ease of use and being free – were also the reasons for the security vulnerabilities of the platform, revealing how insecure and unprotected this platform is.
Zoom was never meant to provide end user experience and was always more business-oriented platform. Founder and CEO of Zoom has admitted and apologized in multiple occasion for not reading the lay of the land and not responding quickly enough
That being said, this article is meant to offer alternatives to zoom or at the very least some settings to help secure the platform better.
Below are few options that are available to most of us who are part of an organization.
Using Your Email Provider’s Platform
Video conferencing has nothing to do with your email provider, however, if you are in the cloud (which majority of us are by now), most likely your email provider has a video conferencing tool available to be used.
Office 365 – If you are using Office 365 as your email provider , you have probably noticed the Microsoft Team icon that keeps bugging us all. Microsoft teams is the revamped Skype for Business (Microsoft has purchased Skype few years ago) and yes, this tool is not great. The ease of use is not there and the quality is not ideal, however it is a free tool and by far more secured then using Zoom these days.
Google Meet – Previously known as Google Hangouts. If your organization uses Gmail as their email platform, Google Meet is free. This is by far, the best tool out there. Everything Zoom can offer, Google Meet offers as well, and the security features of this tool, already built in (no need to be an IT expert to configure it) and are far more advanced than Zoom.
Other Email Platforms – Whether you are using Godaddy, Intermedia, Appriver, or any other 3rd party Email hosting, majority of these tools have some sort of video conferencing. If such tool is available for your organization, it is most likely more secured than using Zoom and probably will not attract hackers due to not being a “mainstream” solution so even if the security of such tools are not as advanced as Google or Microsoft’s the fact it is more of an underground tool, makes it more secure than Zoom who is all over spotlights.
Using your VoIP Provider’s Platform
If your organization is using VoIP technology for phones, most likely you are provided with a video conferencing tool, hopefully at no cost (each provider is different).
In such cases, using that tool can be a great option as well.
Some popular ones are the Intermedia Unite platform or the RingCentral Office platform (AT&T has partnered up with RingCentral so you might have this tool available to you whether you are with AT&T VoIP or directly with RingCentral).
There are many other VoIP tools out there, some are using the Cisco WebEx or the GotoMeeting tools which otherwise would cost a good penny as direct subscription but if you are not sure, inquire with your organization whether such tools are available and again, most likely those tools would be far more secured than Zoom, at least for the time being while Zoom is figuring out a proper way to secure their platform.
Using a Paid 3rd Party Vendor
There are many different Audio/Video conference call tools out there. A lot of the vendors are now stepping up and offering FREE trials or upgraded features to the “Free Tiers” meaning that their tools can assist you to host business meetings or just social virtual gatherings at no cost.
Some of the tools out there would be:
- Cisco WebEx – Offering free options that should meet all of your needs under the free version - Webex Plans and Pricing
- Skype – the individual tool is still free but is limited to 50 participants. The downside is the ease of use with Microsoft’s signing in platform , some might find this frustrating.
- FreeConference.com – Free tool but is very limited for number of attendees - Freeconference Website
There are also few paid tools that you might be interested in exploring, including , but not limited to:
- GoToMeeting – probably the best paid tool out there.
- CyberLink U Meeting
- Zoom Meeting (Paid License) – do not get confused with the free version. The Paid versions do come with improved security features and is a good option if you are willing to pay.
As a personal recommendation, I would test all the free options described above prior to resorting to a paid option. All the options recommended have all the features you need to stay connected, stay production and most importantly stay secured. It is a matter of your ease of use and general liking of the platform, rather than features. Another aspect to consider is platform features and mainly limitations. Does the application support all the participants you are planning to invite to the meeting? Does the application support mobile?
Luckily, all these applications made their features visible and easily accessible on their sites to compare and choose the proper one.
If you have still determined that Zoom is the only platform you are willing to use or got used to, at least follow these recommendations below on how to setup a secured Zoom meeting.
This will not guarantee the safety of your meeting, but it will guarantee the absolute best steps you can take to secure it as much as possible.
If you are still interested in using Zoom , below are recommended settings within the application to have a more secure and encrypted sessions with your attendees:
Setting up a Zoom meeting

Always use the auto generation: every meeting will then have a different Meeting ID. If one Meeting ID becomes compromised, then it will only apply to a single meeting rather than every meeting you host.
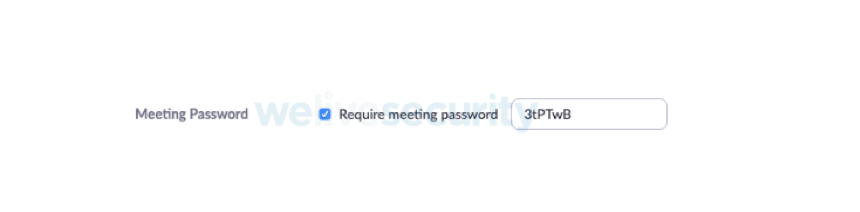
This does not mean a password is required by the user to join: The requirement for a password should remain checked. For it to be effective, however, the embed password option must be disabled; see below.

Starting a meeting with video off avoids any embarrassing moments; users will need to explicitly switch on video sharing during the meeting.
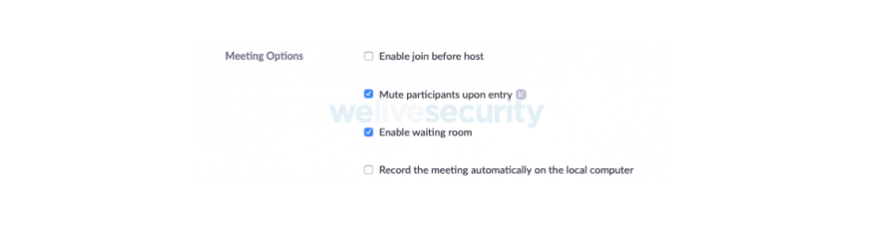
The host will need to admit each participant to the conference room; full attendee control is in the host’s hands.
In the same spirit of video being switched off, forcing someone to unmute means they don’t join while speaking to someone else and being overheard.
There are additional settings that need to be considered; they are available within the web client rather than the Zoom application. After logging in on the left-hand side, click on the ‘Settings’ option that appears under ‘Personal’. Below are the settings that I recommend changing from their default option.
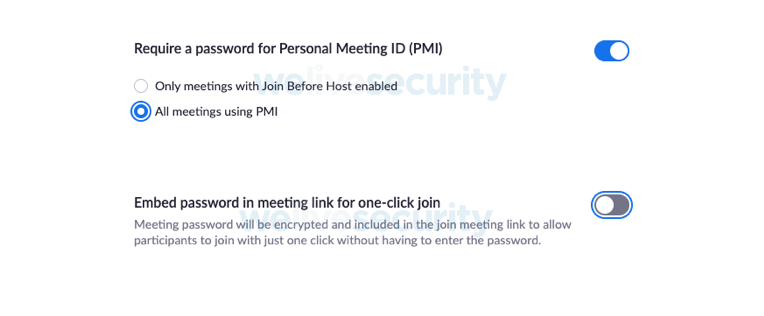
Switching this off removes the one-click option and stops the password being embedded in the meeting link. This means every attendee will need to enter the password to join the meeting. Set this in conjunction with the setting in the meeting creation options as above.
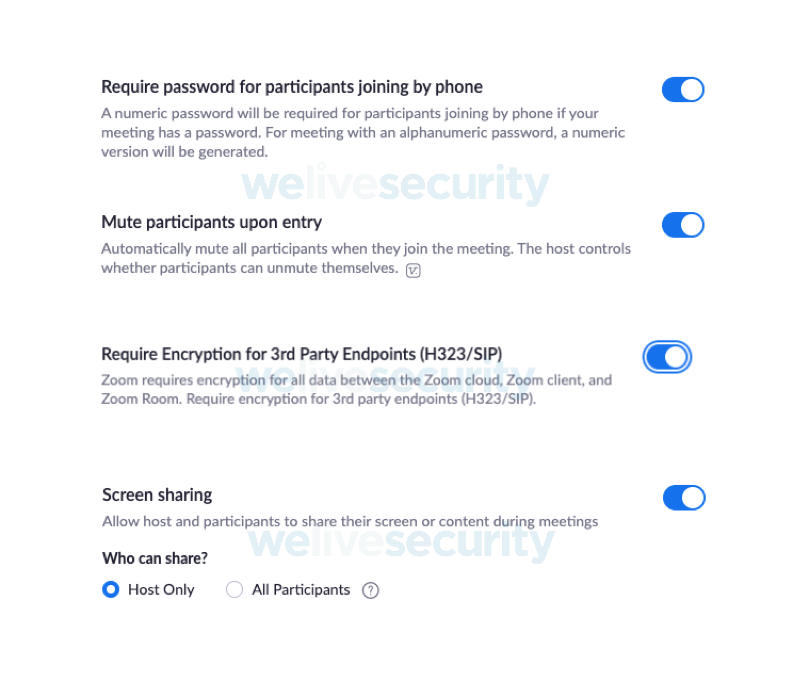
This stops any participant sharing their screen, the host can pass control of the meeting to another participant by making them the host so they can share their screen. This recommendation may not work in all environments; for example, in education it may not be desirable to pass host control to a student. Consider the consequences of allowing all participants to screen share and whether limiting to ‘host only’ is the best option.

Consider switching this off as viewing what’s in the background could be a visual check that a participant is not inadvertently sharing sensitive content in a public place such as a coffee shop.
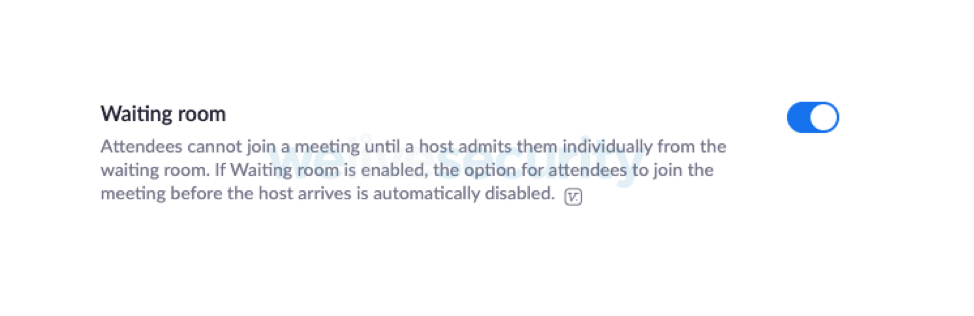
See the description given above in the ‘setting up a meeting’ section.
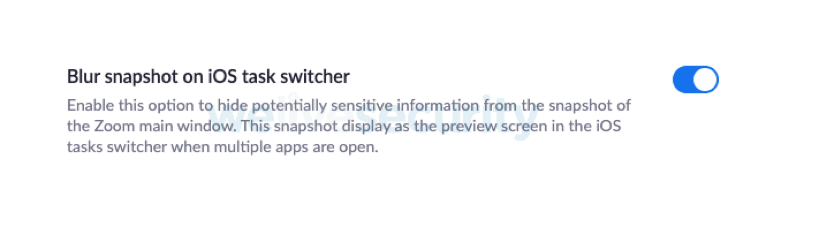
Apple iOS devices screen capture applications to display images in the task switcher; enabling this stops confidential data being captured and displayed in the task switcher.
In conclusion, whatever tool you end up using, make sure you secure it properly. While we are battling in the real world against a pandemic that has been hurting us all, we must stay vigilante against a pandemic that has always lurking around the corner and now has evolved into a way to hurt us all. Even though, it is not receiving its recognition and attention in the media and social media like COVID19, the cyber threat is as serious to our day to day as the viral one.
For questions, concerns or general consulting, fill out the form on the right side and let IT Support LA help!


